

Certificates are issued by a certifying authority (CA), which can be any trusted central administration willing to vouch for the identities of those to whom it issues certificates and their association with a given key. A company may issue certificates to its employees, a university to its students, a town to its citizens. In order to prevent forged certificates, the CA's public key must be trustworthy: a CA must either publicize its public key or provide a certificate from a higher-level CA attesting to the validity of its public key. The latter solution gives rise to hierarchies of CAs. See Figure 14 for an example.
Certificate issuance proceeds as follows. Alice generates her own key pair and sends the public key to an appropriate CA with some proof of her identification. The CA checks the identification and takes any other steps necessary to assure itself that the request really did come from Alice, and then sends her a certificate attesting to the binding between Alice and her public key, along with a hierarchy of certificates verifying the CA's public key. Alice can present this certificate chain whenever desired in order to demonstrate the legitimacy of her public key.
Since the CA must check for proper identification, organizations find it convenient to act as a CA for its own members and employees. There are also CAs that issue certificates to unaffiliated individuals.
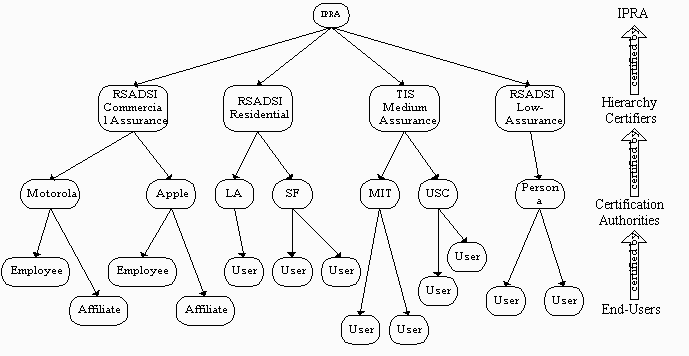
Different CAs may issue certificates with varying levels of identification requirements. One CA may insist on seeing a driver's license, another may want the certificate request form to be notarized, yet another may want fingerprints of anyone requesting a certificate. Each CA should publish its own identification requirements and standards, so that verifiers can attach the appropriate level of confidence in the certified name-key bindings. CA's with lower levels of identification requirements produce certificates with lower "assurance." CA's can thus be considered to be of high, medium, and low assurance. One type of CA is the persona CA. This type of CA creates certificates that bind only e-mail addresses and their corresponding public-keys. It is designed for users who wish to remain anonymous yet want to be able to participate in secure electronic services.
An example of a certificate-issuing protocol is found in Apple Computer's System 7.5 for the Macintosh. System 7.5 users can generate a key pair and then request and receive a certificate for the public key; the certificate request must be notarized.
VeriSign, Inc. provides a complete line of certificate-related
products and services; see <http://www.verisign.com/>
for more information.