

When we use a block cipher to encrypt a message of arbitrary length, we use techniques that are known as modes of operation for the block cipher. Modes must be at least as secure and as efficient as the underlying cipher. Modes may have properties in addition to those inherent in the basic cipher. The standard DES modes (see Question 66) have been published in FIPS PUB 81 [NIS80] and as ANSI X3.106 [ANS83]. A more general version of the standard [ISO92b] generalized the four modes of DES to be applicable to a block cipher of any block size. The standard modes are Electronic Code Book (ECB), Cipher Block Chaining (CBC), Cipher Feedback (CFB), and Output Feedback (OFB).
In ECB mode (see Figure 3), each plaintext block is encrypted independently with the block cipher.
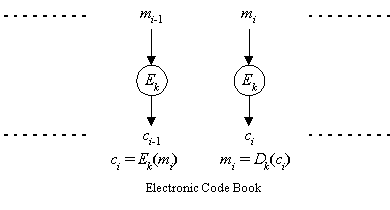
Figure 3. Electronic Code Book Mode
ECB mode is as secure as the underlying block cipher. However, plaintext patterns are not concealed. Each identical block of plaintext gives an identical block of ciphertext. The plaintext can be easily manipulated by removing, repeating, or interchanging blocks. The speed of each encryption operation is identical to that of the block cipher. ECB allows easy parallelization to yield higher performance. Unfortunately, no processing is possible before a block is seen (except for key setup).
In CBC mode (see Figure 4), each plaintext block is exclusive-ored with previous ciphertext block, then encrypted. An initialization vector or value c0 is used as a "seed" for the process.
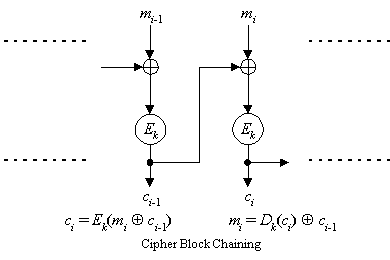
Figure 4. Cipher Block Chaining Mode
CBC mode is as secure as the underlying block cipher against standard attacks. In addition, any patterns in the plaintext are concealed by the exclusive-oring of the previous ciphertext block with the plaintext block. Security of the ciphertext is enhanced as the plaintext cannot be directly manipulated except by removal of blocks from the beginning or the end of the ciphertext. The speed of encryption is identical to that of the block cipher, but the encryption process cannot be easily parallelized though the decryption process can be parallelized.